What Is the 5.4.13 Lab: Secure a Small Wireless Network is a hands-on learning exercise designed to teach you how real wireless security works in everyday environments. Many students in the United States encounter this lab in a Cisco networking lab or NetAcad wireless lab setting. It focuses on building a secure small wireless network using realistic tools and settings you will see in homes and small offices.
This wireless network security lab is not theory-heavy. Instead, it shows how mistakes happen and how attackers exploit weak Wi-Fi. By completing the 5.4.13 networking lab, you practice hands-on network security and learn how protecting a Wi-Fi network works in the real world. That is why this lab matters far beyond grades.
Why Securing a Small Wireless Network Is Important in This Lab
Security matters because wireless networks are invisible. Anyone nearby can try to connect. In the 5.4.13 Lab: Secure a Small Wireless Network, you start with weak settings to see how easy it is to break into a network. This approach helps you understand why wireless security is important instead of just memorizing rules.
In real life, a poor small network security setup can expose private data. Weak passwords, open SSIDs, and loose network firewall settings invite trouble. This lab teaches practical wireless security by showing how small changes can block real attacks and prevent long-term damage.
Basic Network Setup Used in the 5.4.13 Wireless Security Lab
The lab uses a simple design that mirrors a typical home network security setup in the US. A wireless router connects laptops and desktops. At first, the router uses default settings. This makes the network easy to access but unsafe. That unsafe starting point helps you see risks clearly.
During the lab configuration steps, you learn how wireless router configuration affects every device. You work with IP addresses, wireless clients, and router interfaces. This basic wireless security lab setup helps beginners understand how small networks really function.
How to Secure a Wireless Router Step by Step
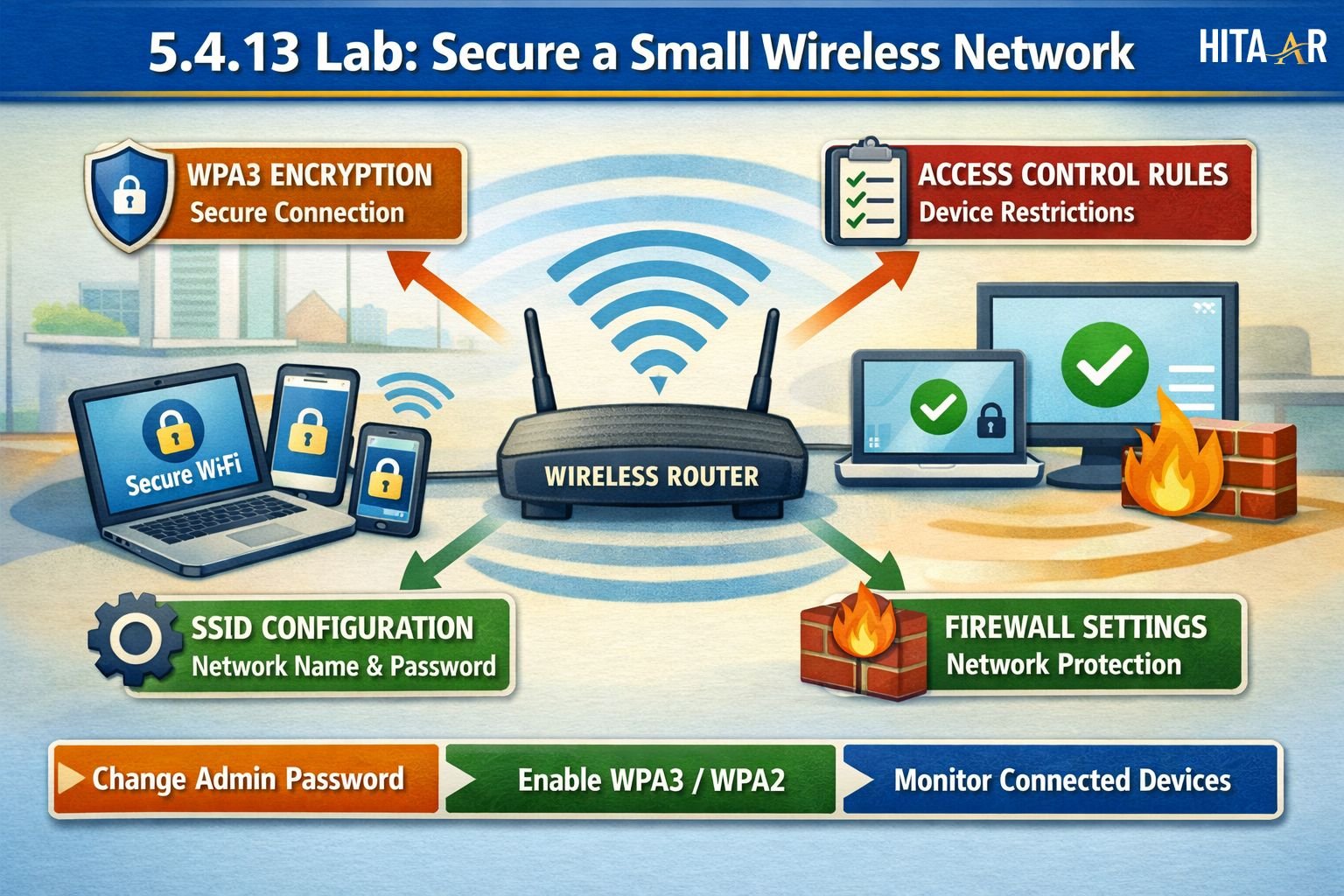
Security begins at the router. In the 5.4.13 Lab: Secure a Small Wireless Network, you log in and immediately change weak defaults. Admin password security is the first defense. Strong credentials stop attackers before they even reach Wi-Fi settings.
Next comes SSID configuration and encryption. Enabling WPA2 wireless security or WPA3 encryption protects data in motion. You also review access control rules and wireless authentication. These steps form the backbone of a secure small wireless network that resists common attacks.
Using Simple Network Management Protocol in a Small Network
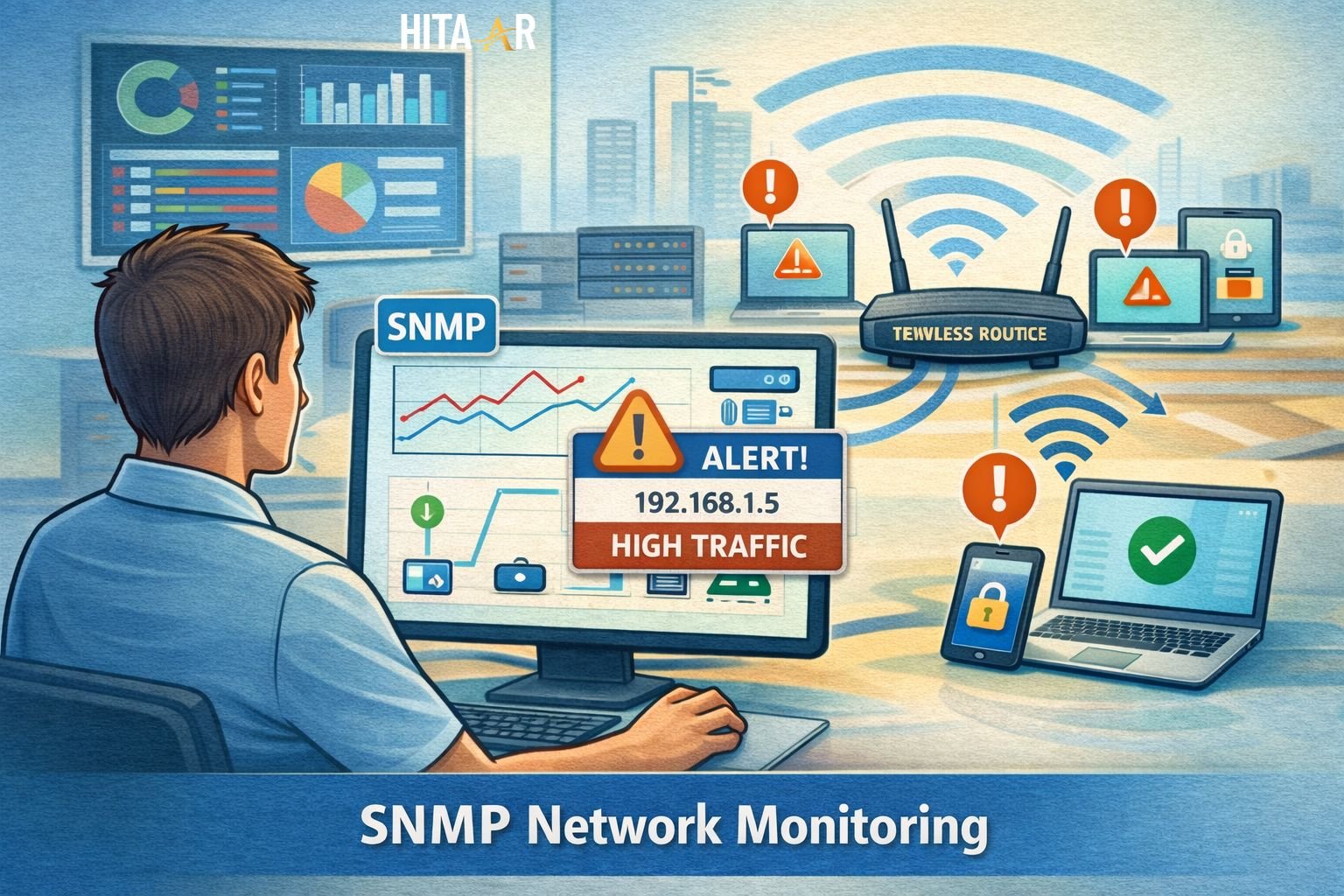
The lab introduces simple network management protocol to show how devices communicate status information. Many beginners overlook monitoring. This is where SNMP configuration basics matter. Proper settings help administrators see problems early.
However, SNMP security risks are real. Weak SNMP community strings can expose device data. In the lab, you explore SNMP network monitoring safely. You learn managing devices with SNMP using trusted network management tools without opening security holes.
Common Wireless Security Settings Explained Simply
Wireless security sounds complex, but the lab breaks it down. Encryption protects data. Firewalls filter traffic. Authentication confirms identity. Together, these create a reliable wireless security configuration that protects users without slowing the network.
You also learn why unused features create risk. Turning off weak services strengthens secure router settings. This section reinforces protecting a Wi-Fi network using logic instead of guesswork, which is essential for beginner network security learners.
Why You May See “You’ve Been Blocked by Network Security”
Seeing you’ve been blocked by network security often scares students. In truth, it usually means the system is working. A wireless security restriction activates when credentials fail or rules are broken.
Messages like network access blocked, firewall blocking connection, or blocked by router security appear when policies detect risk. These alerts prevent a network policy violation and stop unwanted access before damage occurs.
How to Fix Network Security Blocks During the 5.4.13 Lab

Fixing issues requires patience. In the 5.4.13 Lab: Secure a Small Wireless Network, you review passwords, encryption, and firewall rules. Most errors come from mismatched settings rather than broken hardware.
Understanding how to fix blocked network access helps you avoid shortcuts. Instead of disabling security, you adjust rules properly. This teaches real-world troubleshooting for connection denied by network errors without weakening protection.
How to Check If Your Small Wireless Network Is Secure
Validation matters. After configuration, you confirm encryption, authentication, and network traffic monitoring. Checking connected devices ensures no unknown users slipped in during setup.
This step shows whether how to secure a small wireless network was done correctly. You verify firewall behavior, review logs, and confirm stability. These checks transform theory into confidence and reinforce monitoring small networks effectively.
Key Lessons Learned from the 5.4.13 Secure Wireless Network Lab
The biggest lesson is mindset. Security is proactive. The 5.4.13 Lab: Secure a Small Wireless Network teaches you to think ahead, not react later. You learn that small choices create big outcomes.
Students leave with skills they can use anywhere. From dorm Wi-Fi to small offices, this lab builds confidence in small Wi-Fi network protection. It prepares you for advanced networking while grounding you in real, usable security knowledge.
FAQs
How to create a secure wireless network?
To create a secure small wireless network, start by changing the default admin username and password on your router. Enable WPA2 wireless security or WPA3 encryption to protect data in transit. Set a strong, unique SSID and password. Enable the firewall, turn off unnecessary features, and monitor connected devices regularly. These steps ensure your network remains safe from common attacks.
Which settings in a wireless access point can you configure to improve security?
You can improve security by adjusting several key settings. Change the SSID configuration to hide your network if needed. Enable wireless authentication, use strong encryption like WPA3, and configure access control rules to restrict unknown devices. Regularly update router firmware, enable network traffic monitoring, and secure admin password security to prevent unauthorized access.
What is one common method used to secure a wireless network?
One of the most common methods is enabling WPA2 or WPA3 encryption on the wireless router. This ensures that all communication between devices is encrypted, making it much harder for attackers to intercept data. Combined with strong passwords, firewall rules, and wireless security configuration, this method forms the backbone of practical wireless security.
What is the first security measure the technician should apply immediately upon powering up the wireless router?
The very first step is to change the default admin credentials. Admin password security is critical because default usernames and passwords are widely known and can allow anyone to access your router. After that, configure the SSID and enable WPA2 or WPA3 encryption. These simple steps immediately protect your secure small wireless network from unauthorized access.
Stay updated with the latest tech and networking news on Hitaar